Hello Friends,
Let us discuss about the Vsftp configuration, chroot FTP and how to secure the FTP with SSL. You all are aware about what is vsftpd. vsftpd (Very Secure FTP Daemon) is an FTP server for UNIX-like systems, including CentOS / RHEL / Fedora and other Linux distributions. It supports IPv6, SSL, locking users to their home directories and many other advanced features.
This is the complete configuration guide for VsFTP hence this post is bit long. Request to read completely !
Let us first install the package for configuring the vsftpd. Install the vsftpd using yum or with rpm -ivh. here i have a Yum server configured hence i am using a Yum to install this package.
Let us first install the package for configuring the vsftpd. Install the vsftpd using yum or with rpm -ivh. here i have a Yum server configured hence i am using a Yum to install this package.
#yum install vsftpd
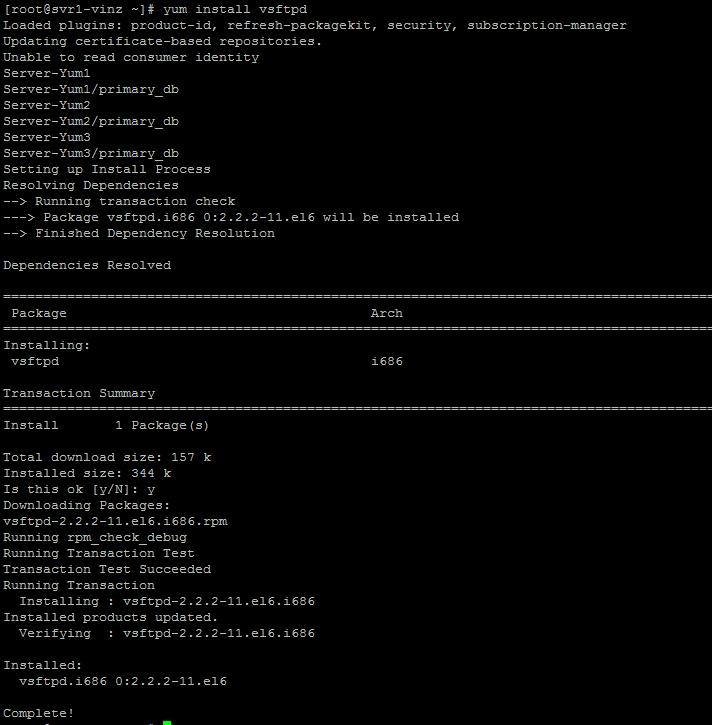
Verify the package after installation using rpm –ql vsftpd this will give us the details about the configuration files and directory structure that vsftpdprovides.
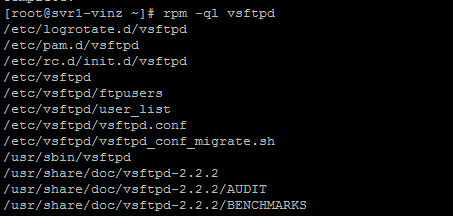
The following directories will be created after the vsftpd installation. This /var/ftp and /var/ftp/pub directories are public directories where the anonymoususer will go after the anonymous FTP login.

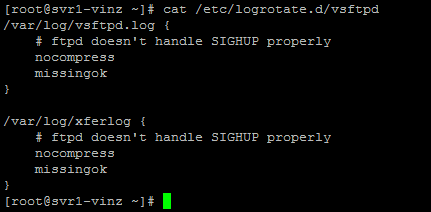
/etc/logrotate.d/vsftpdis the file which used for log rotation. You can see the contents below.
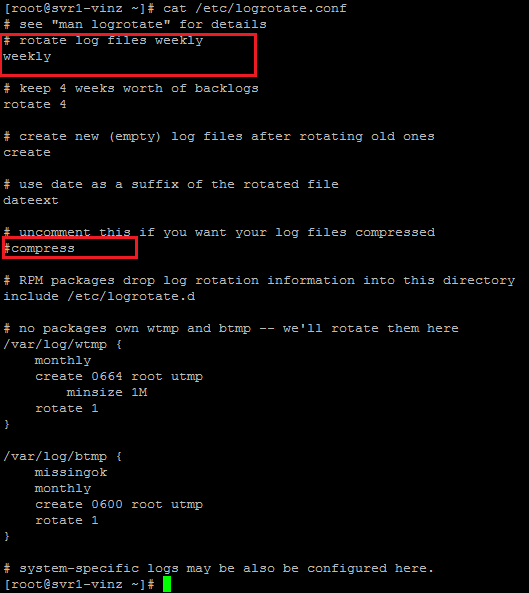
How log rotate will happen,the frequency and other settings will be in /etc/logrotate.conf file. Here is the screen shot. This configuration file is common for all daemons for handling the logs.
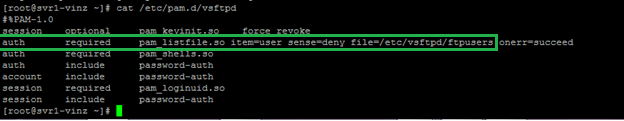
Pam authentication rules for vsftp is found in the following file. For example you can see the
/etc/vsftpd/ftpusers file mentioned. The users in the ftpusersfile will be denied ftp access.
Now let us check the vsftpd configuration location and checkout the files and usages.
Vsftp configuration files will be under /etc/vsftpd directory
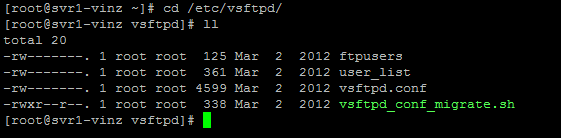
Let us checkout what is the content of ftpusers file. This file contains the users that are not allowed to access/login via ftp. By default you can see user root and all the service daemons are not allowed.
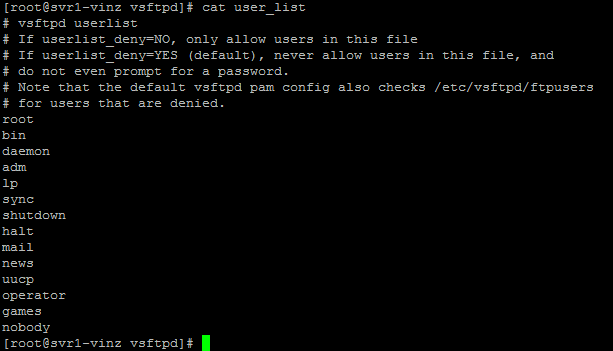
The user_list file contain the same contents in the ftpusers file, however using this file we can control the access to users and we can mention this file in the vsftpd.conf file.
Now the main configuration file /etc/vsftpd/vsftpd.conf file .This is the file where we can change a lot of attributes of FTP access and its configurations.
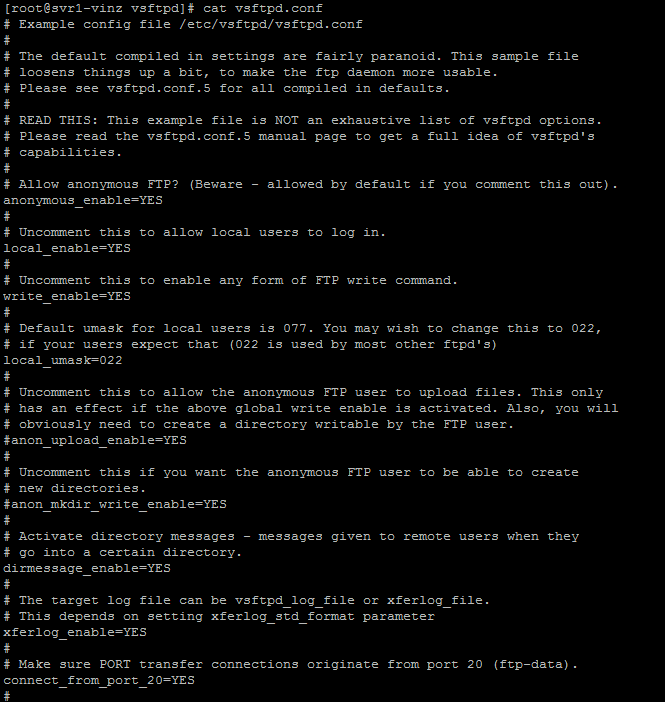
These are the following directives that control the characteristics of VSFTP. Also you can check the man vsftpd.conf command to check out for more option.
anonymous_enable=YES
local_enable=YES
write_enable=YES
#anon_upload_enable=YES
#anon_mkdir_write_enable=YES
dirmessage_enable=YES
xferlog_enable=YES
connect_from_port_20=YES
#chown_uploads=YES
#chown_username=whoever
#xferlog_file=/var/log/xferlog
xferlog_std_format=YES
#idle_session_timeout=600
#data_connection_timeout=120
#nopriv_user=ftpsecure
#async_abor_enable=YES
#ascii_upload_enable=YES
#ascii_download_enable=YES
#ftpd_banner=Welcome to blah FTP service.
#deny_email_enable=YES
# (default follows)
#banned_email_file=/etc/vsftpd/banned_emails
#chroot_local_user=YES
#chroot_list_enable=YES
# (default follows)
#chroot_list_file=/etc/vsftpd/chroot_list
#ls_recurse_enable=YES
listen=YES
#listen_ipv6=YES
pam_service_name=vsftpd
userlist_enable=YES
tcp_wrappers=YES
By default the vsftpd daemon will not be running. You need to manually enable the vsftp in multiuser mode using chkconfig command.
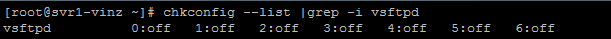
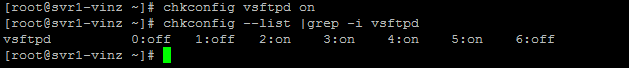
Run “chkconfig vsftpd on” to enable the vsftpd in multiuser mode.
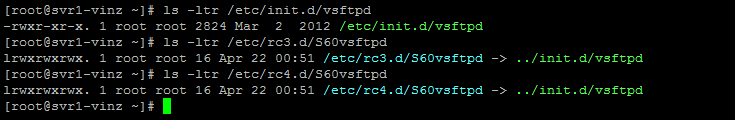
To double confirm that whether it is enabled or not you can check rc run level directories like below.
Now we can start the vsftpd service using servicecommand.
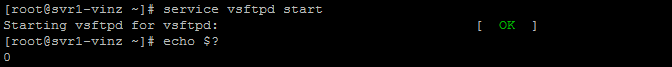
Verify which port vsftpd is listening, you can verify it using netstat –ntlp |grep –i 21
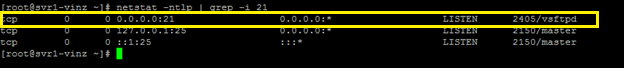
As I mentioned earlier by default the vsftpdwill allow the anonymous access. Let us try to access the ftp from a browser. I am using firefox and trying to access my FTP server.
Yes I am able to access the FTP server anonymously!!
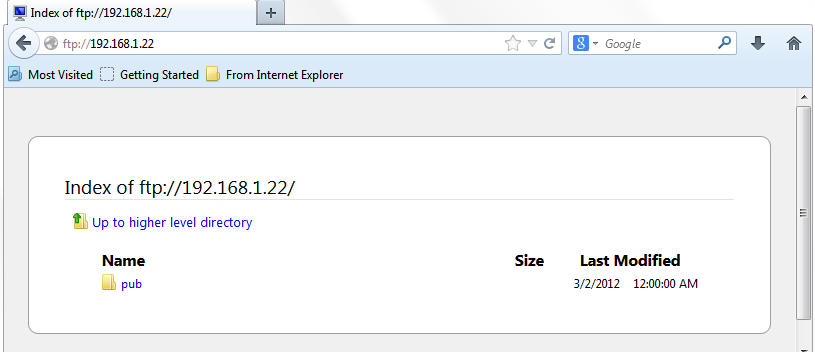
Here is the command line test for anonymous login. You need to enter username as “anonymous” and password is just press enter or put any word or email address.
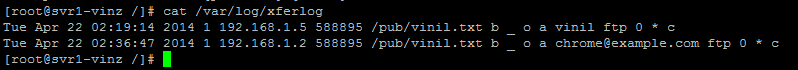
Let us try a file download option. Create a simple file under /var/ftp/pub directory using seq command.
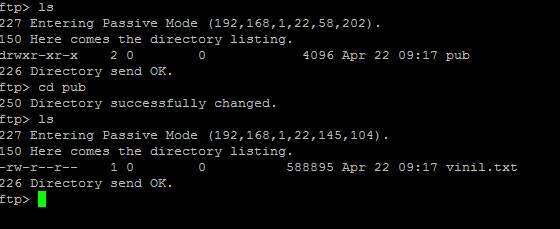
Open the ftp session as anonymous and try to download the this file.
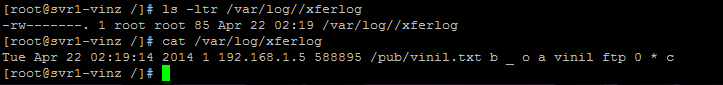
now checkout the xferlog log file located under /var/log directory you could find the entry for the file download that we just tried above.
I have checked some more scenarios and I could see that Vsftpddoes not support ipv4 and ipv6 simultaneously. It can work either with only IPV4 or IPV6.
Now let us disable the anonymous login and try the FTP with user based authentication.
Edit the /etc/vsftpd/vsftpd.conf file and change the following line
Anonymous_enable=NO
Now restart the vsftp service to load the new configuration.
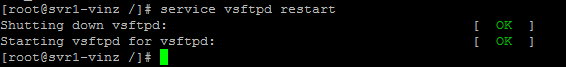
Let us try login as anonymous user and check now. Whether we are able to login as anonymous user or not. Yes its blocking we are unable to login as anonymous.
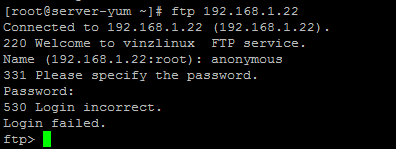
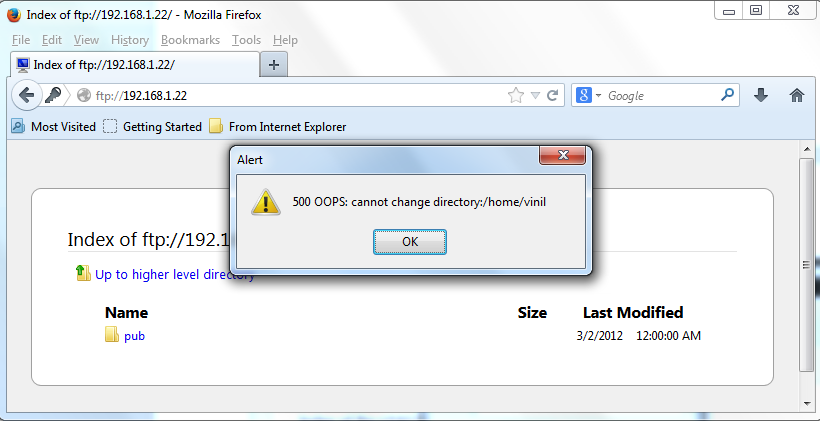
So now the anonymous login is disabled and now let us try to login as a user vinil and try giving the password. I am trying to login as vinil and given the password however I am getting an error “500 OOPS: cannot change directory: /home/vinil
Login failed.
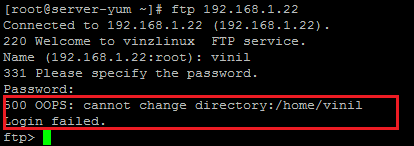
Checked using the browser however I got the same error even I am giving the right password.
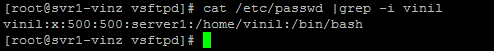
Let us verify the password file and home directory permission of user “vinil”
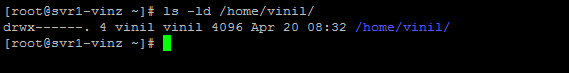
It seems the permission is fine and why we are getting this error “500 OOPS: cannot change directory: /home/vinil”
Let us check the SElinux status and the selinux policy set for FTP.
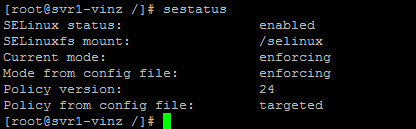
Looking into SElinux policy for FTP I could see that the policy/Boolean “ftp_home_dir àoff”. So this is the reason for not allowing to change the home directory.
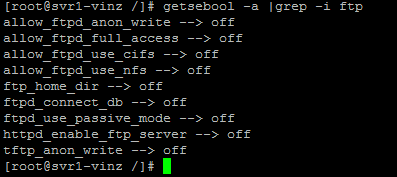
Run setsebool command to enable the ftp_home_dir à on.
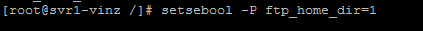
Once the above command is finished then double check again.
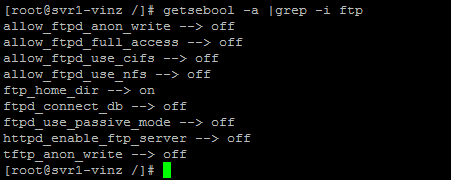
Now to test the login with user vinil. Now we are able to login successfully!
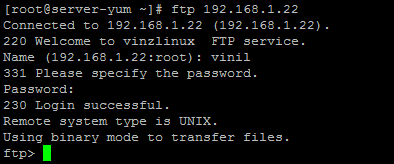
Use your browser to ftp using the user “vinil”.
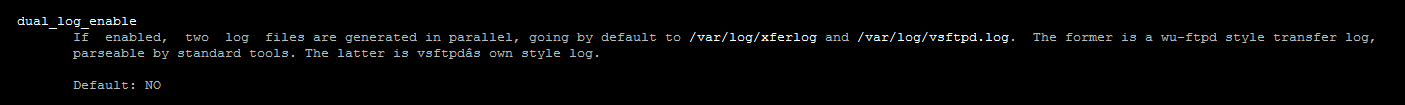
Dual logging in VSFTP:
Let us check how to enable the Dual logging in VSFTP.
Run man vsftpd.conf command and check the man page for the following portions:
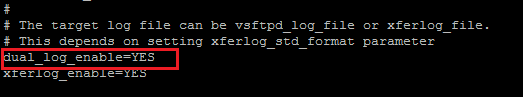
Now edit the /etc/vsftpd/vsftpd.conf file and enter the following entry.
After this we need to restart the vsftpd daemon to effect this change.
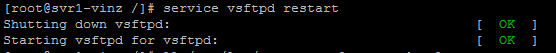
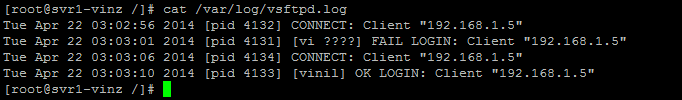
Once the daemon is successfully restarted check the log files. We could see /var/log/xferlog and /var/log/vsftpd.logfiles.
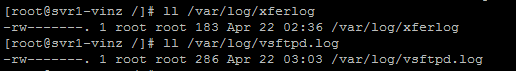
You could open and see the contents it would have the details of FTP session and transfer information.
You can add many features like time setting etc in the vsftp configuration file. I would recommend to read the manpage of vsftpd.conf for more information.
That’s all about the simple vsftpd configuration!
Securing the FTP using SSL:
Now let us discuss about securing the FTP using SSL. In other words FTPS (FTP over SSL). We all are aware that the FTP uses clear text in communication so basically it is not secure.
Let us see what is the threat in FTP. I have enabled the tcpdump and trying to access the ftp. Run the below command to enable the tcpdumptracing (I have enabled the tracing in my FTP server for testing).
tcpdump -v -Ae tcp port 21
From the client machine I am connecting using ftp command, shown below.
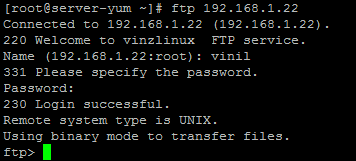
Now check tcpdump window and see the result. Here you could see the username and password is human readable format. So this is a threat!!
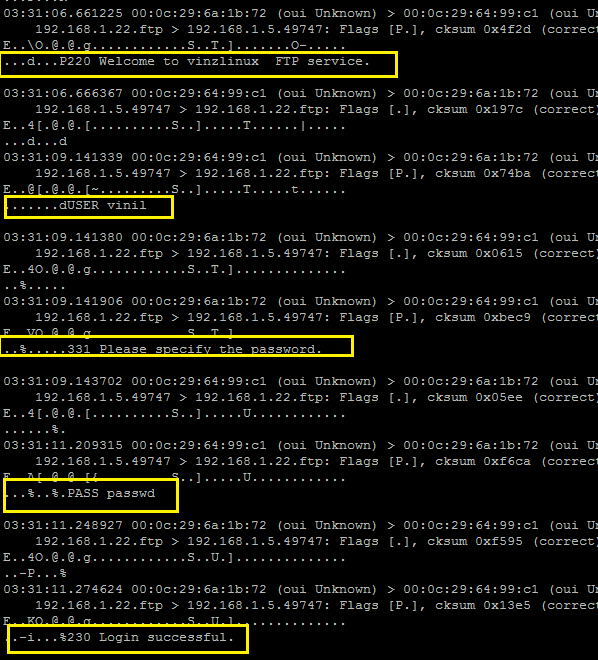
Here I am discussing about how to secure FTP using SSL. This will enable the Encryption of data and control channel.
There are 2 modes of FTP over SSL available. They are implicit and explicit mode. Implicit uses TCP port 990 and Explicit uses TCP port 21.
Here I am explaining about the explicit mode. For using FTP over SSL we need to have a certificate first. Certificate can be either self-signed or signed by CA or Verisign etc.
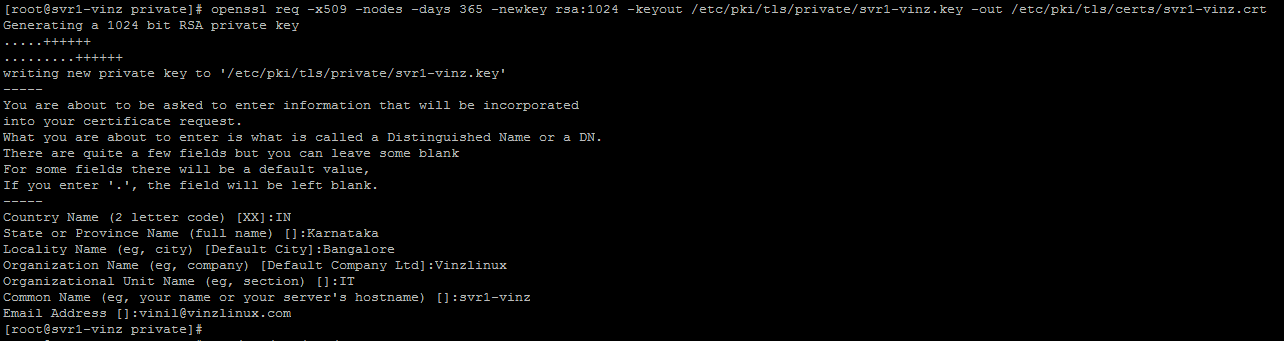
I am using a self-signed certificate here. Let us create a certificate using openssl command
openssl req -x509 -nodes -days 365 -newkey rsa:1024 -keyout /etc/pki/tls/private/svr1-vinz.key -out /etc/pki/tls/certs/svr1-vinz.crt
This command will create an rsa 1024 private and public certificate using /etc/pki/tls/private & /etc/pki/tls/certs
Once you ran the command you could see the below screen and you need to enter the details like name of the organization, country, e-mail address etc.
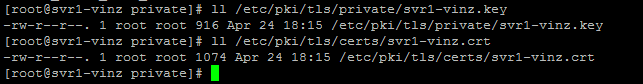
Once the command executed successfully checkout the directories to see the public and private certificates. And.... yes its available!!.
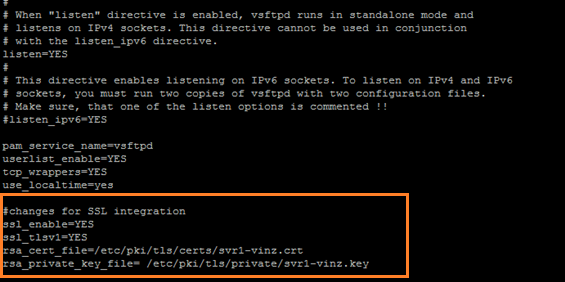
Next you need to edit the vsftpd.conf file and add the SSL enable and certificate details in the configuration. So that vftpd will now start using the SSL.
ssl_enable=yes àthis will require local logins (non-anonymous user) to use SSL /TLSv1
ssl_tlsv1=yes àdefault protocol
rsa_cert_file= /etc/pki/tls/certs/svr1-vinz.crt àthis file allow the vsftpd to read both private and public key
rsa_private_key_file= /etc/pki/tls/private/svr1-vinz.key àset this if the private key in a different file
Now restart vsftpd daemon to load the changes that we made now.
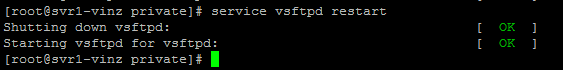
Now let us try to login using ftp command you will not be able to login now. You would see a message “530 Non-anonymous session must use encryption”
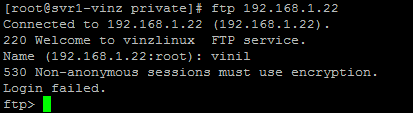
Our normal FTP command does not support encryption so we need to use lftp command.
For using lftp we need to install lftppackage.
Here I am installing the lftp package using YUM server.
Simply run the following command to login to lftp to check the environment variables.
#lftp 192.168.1.22
[root@svr1-vinz ~]# lftp 192.168.1.22
---- Resolving host address...
---- 1 address found: 192.168.1.22
lftp 192.168.1.22:~>
Now run “set –a |grep –i ssl” at the prompt to check the variable for ssl.
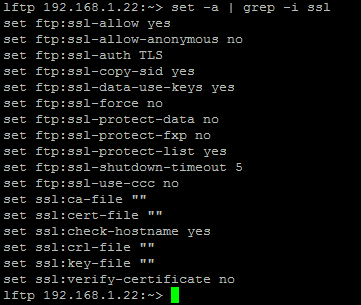
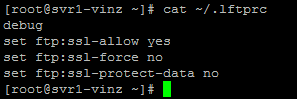
We need FTP to use ssl for encryption. For that we need to create .lftprc file in the home directory (client side)and enter the following details.
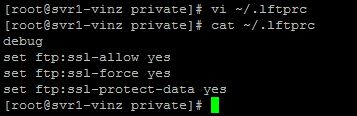
Once the above settings are done then run the lftp command to access ftp service.
#lftp username@192.168.1.22enter the credentials ,now you would be able to see that FTP session is using SSL and TLS .Also you could see the certificate details (highlighted in yellow).
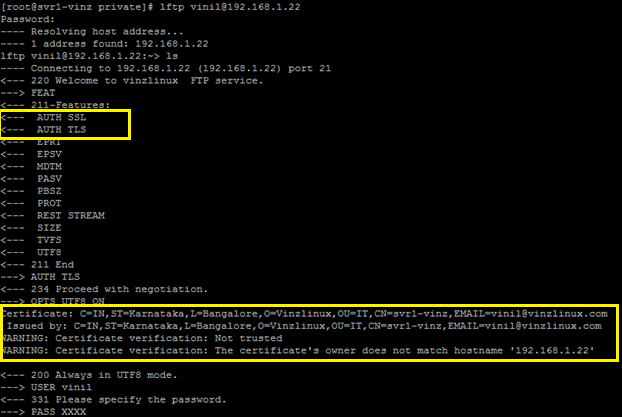
It looks perfectly fine now let us check the GUI based login from a windows client machine.
I am using WinSCP software here to connect to my FTP server. Checkout the session details I use “SSL Explicit Encryption” in encryption type.
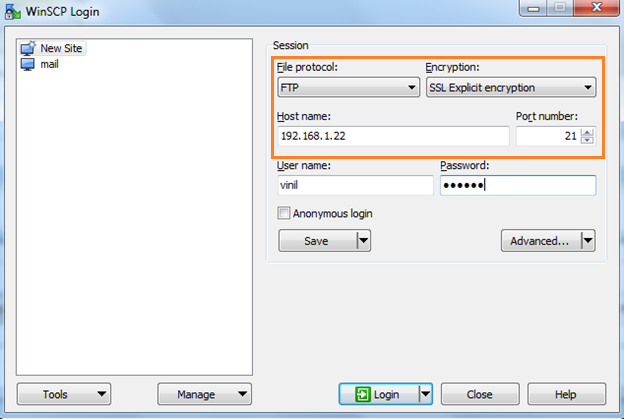
Click on login you could see a pop-up window which contain the certificate that we have integrated to FTP server.
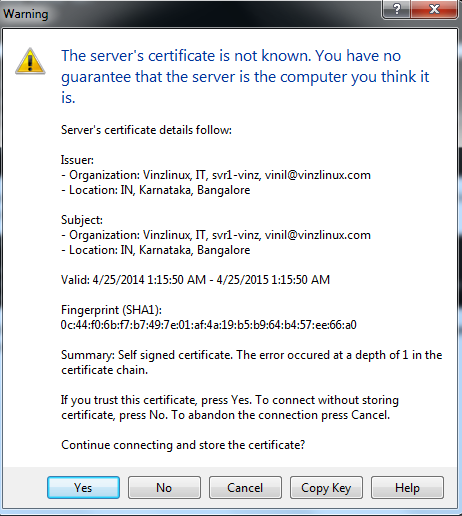
Click “Yes” and you could see the window for entering the password. You can find the TLS connection in the password window.
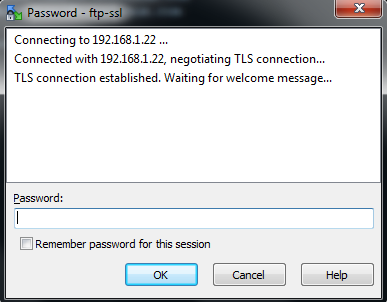
After you entered the password click “OK” now you would be able to land in the FTP server.
We can also configure the vsftp with SSL/TLS and Clear Text communication. There is a small modification needs to be done in the /etc/vsftpd/vsftpd.conffile and .lftprc file. However it still uses the certificate that we integrated to FTP. In some scenarios we might need to have both clear text as well as encryption.
Entries that need to be added in the vsftpd.conf file
Entries for .lftprc file
FTP jailing:
This document is already lengthy. Before ending this document I would like to add the FTP jailing. I am explaining the very basic step for FTP jailing (Chrooted FTP).
"Jailing" in ftp means locking the ftp session to a particular subset of the filesystem. Usually it is set so that if a particular user logs in, they can only go to their own directory space.
The ftp server will often have an option that, when a user is connected, to chroot the user, which means as far as that user is concerned, the root of the universe is some specific portion of the total available filesystem.
Edit the /etc/vsftpd/vsftpd.conf file and change the following line.
Chroot_local_user=YES
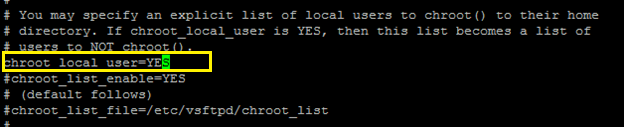
Now restart the vsftpd daemon to learn the changes in the vsftpd.conf
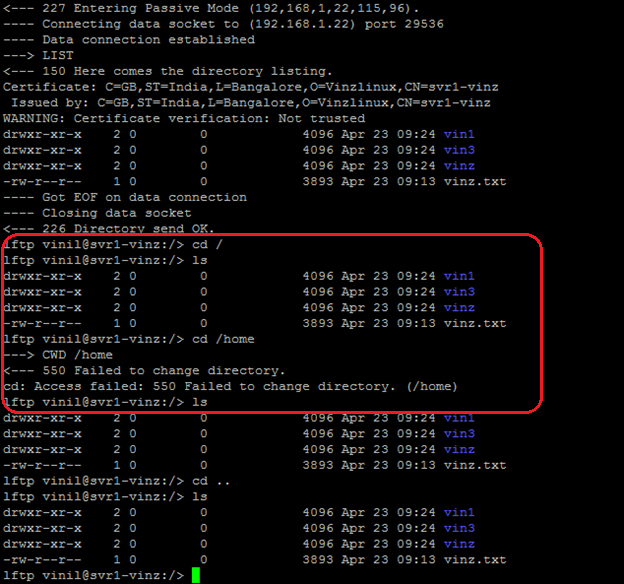
Now try logging in to FTP and try to change the directory to / or any other directory. You would be in the Home directory of the particular user who is logged in.
That’s All Friends about the VsFTPconfiguration. I tried my level best to add all most all configurations in vsftpd in this document. I would like to hear the feedback from your end on this!!
Hi Vinil,
ReplyDeleteI think it is possible to use IPv4 and IPv6 at the same time. It should be enough to set the option
listen_ipv6=YES
it will listen on IPv4 also.
The only problem I had with that was that I had to use NAT on IPv4 and passive mode only worked for IPv4 _or_ IPv6 because I had to give
pasv_address=
and wasn't able to give both, IPv4 and IPv6.
Hi Erik, It won't work for VsFTP.. Thats what i found it.. however i will consider your opinion and will check on it. thank you for checking my blog. !
DeleteHi Vinil, nice article.
ReplyDeleteI have a question on how to enable users to move to different folders. I disabled chrooting but it still does not let me navigate to other directories. Just allows users to be in their home folders. We have a small mount point for home folders and would like to create a seperate directory where users can upload files to for example /FTPFolder which is a seperate mount point, but I am not able to do it now. Any help?